| Abstract | Download | Project Staff |
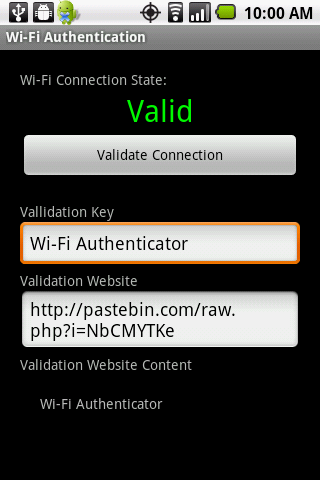
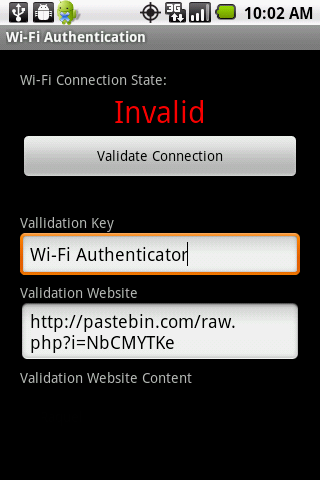
In this paper, we present a novel denial-of-service attack targeted at popular smartphones that are used by normal users who are not technology savvy. This type of attack, which we call a denial-of-convenience attack, prevents non-technical savvy victims from utilizing data services by exploiting the connectivity management protocol of smartphones when encountered with a Wi-Fi access point. By setting up a fake Wi-Fi access point without Internet access (using a simple device such as a laptop computer), an attacker can prompt a smartphone with enabled Wi-Fi features to automatically terminate a valid mobile broadband connection and connect to this fake Wi-Fi access point. This, as a result, prevents the targeted smartphone from having any type of Internet connection unless the victim is capable of identifying the attack and manually disabling the Wi-Fi features. We demonstrate that most popular smartphones, including iPhone and Android phones, are vulnerable to denial-of-convenience attacks. To address this attack, we propose implementing a novel Internet-access validation protocol that uses the cellular network to send a secret key phrase to an Internet validation server. Then, it attempts to retrieve this secret key phrase via the newly established Wi-Fi channel to validate the Wi-Fi access point. We have fully developed and evaluated the attacks as well as the defense prototypes that run on Android phones.
Here is the technical paper
describing this research.
Please note: These prototypes are intended for demonstration purposes only. It may have security vulnerabilities and programming bugs.