We are targeting the testing and vulnerability identification issues in both software and hardware applications. First, in software aspect, software security is one of the most critical problems for computer systems. At the core of the problem of securing software, there are several tasks involving binary analysis we believe can be automated through the novel application of machine learning concepts. By automating them as we outline in this proposal, security analysts will be freed from tedious manual software evaluation, which will decrease development costs, increase productivity, and more efficiently direct resources spent securing software. There are three main challenges facing security analysts that we will address in this proposal: (1). driving programs down specific execution paths; (2). maximizing localized code coverage for software testing; and (3). automating protocol reverse engineering. Second, our approaches will be able to address hardware validation and vulnerability identification issues in the area of firmware or openly available RTLs. Such hardware has the similar design structure and principle as software, and hence, it could also be addressed by our approaches.
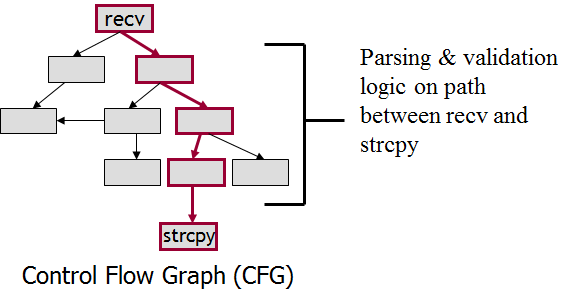
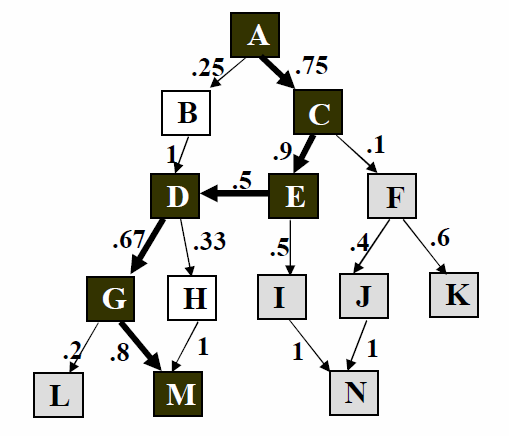
Figure 2: Markov probabilities associated with state transitions on a control flow graph. The white and black squares represent nodes on a control flow path from a given source node (A) to a destination node (M). The grey squares represent reject nodes (nodes from which it is no longer possible to reach the destination node (M) ). The black squares represent the path taken by an arbitrary input through the control flow logic. This path consists of node transitions A->C->E->D->G->M. We can calculate the fitness of this input by multiplying the edge transition probabilities: Fitness = 1 / (.75 * .9 * .5 * .67 * .8) = 5.525
[1]. Sherri Sparks, Ryan Cunningham, Shawn Embleton, Cliff C. Zou. "Automated Vulnerability Analysis: Leveraging Control Flow for Evolutionary Input Crafting", in 23rd Annual Computer Security Applications Conference (ACSAC), p.477-486, Miami Beach, Florida, Dec. 10-14, 2007. (acceptance ratio: 40/191=21%) Best Student Paper Award
[2]. Sherri Sparks, Shawn Ambleton, Cliff C. Zou. "A Chipset Level Network Backdoor: Bypassing Host-Based Firewall & IDS", Proceedings of ACM Symposium on Information, Computer and Communications Security (ASIACCS), Sydney, Australia, 10-12 Mar 2009. (full paper, acceptance ratio: 33/147 = 22.5%)
[3]. Shawn Embleton, Sherri Sparks, Cliff C. Zou. "SMM Rootkits: A New Breed of OS Independent Malware", in Proceedings of 4th International Conference on Security and Privacy in Communication Networks (SecureComm), Istanbul, Turkey, Sept. 22-25, 2008. (full paper, Acceptance ratio: 26/123=21%)
[4]. Shawn Embleton, Sherri Sparks, Cliff C. Zou, "SMM Rootkit: A New Breed of OS Independent Malware", to appear in Wiley Journal of Security and Communication Networks.
[5]. Sherri Sparks, Shawn Embleton, Cliff C. Zou. "Windows Rootkits - a Game of "Hide and Seek",in Y. Xiao, F.H. Li, and H. Chen (Eds): Handbook of Security and Networks,Chapter 19, to be published by World Scientific Press.